Are Your Employees Using DeepSeek? Top Shadow AI Security Concerns


DeepSeek, a Chinese-developed AI platform, has become an overnight sensation, becoming the most downloaded free app in the U.S. and U.K. What’s all the hype about? DeepSeek’s AI models, which are on par or better than industry-leading large language models (LLMs) developed in the US, are available at a fraction of the price. And they require significantly less resources to maintain and scale.
Antiquating even the most cutting-edge AI platforms like ChatGPT and Meta AI, DeepSeek’s high-speed rise to stardom has completely upended the AI market, with Nvidia’s market value falling nearly $600 billion since DeepSeek’s release. That’s the largest single-day drop for any company in history.
Naturally, this has sparked a lot of excitement among technology users, as efficiency-hungry employees race to put the platform to work to replace their now less-impressive AI platforms. For companies with employees embracing the tool, this could mean efficiency gains. But do the benefits outweigh the risks? Short answer: probably not.
The unauthorized use of DeepSeek introduces issues for Security teams by exacerbating an already annoying problem: shadow AI.
Shadow AI Security Concerns for DeepSeek
Shadow AI refers to the unauthorized use of AI platforms within organizations. By utilizing AI tools without IT or Security knowledge, employees often unknowingly expose their organization to risks such as data privacy issues, compliance violations, and disinformation that could influence operations.
Here are the top shadow AI security concerns for organizations with DeepSeek users:
Data Transmission to China
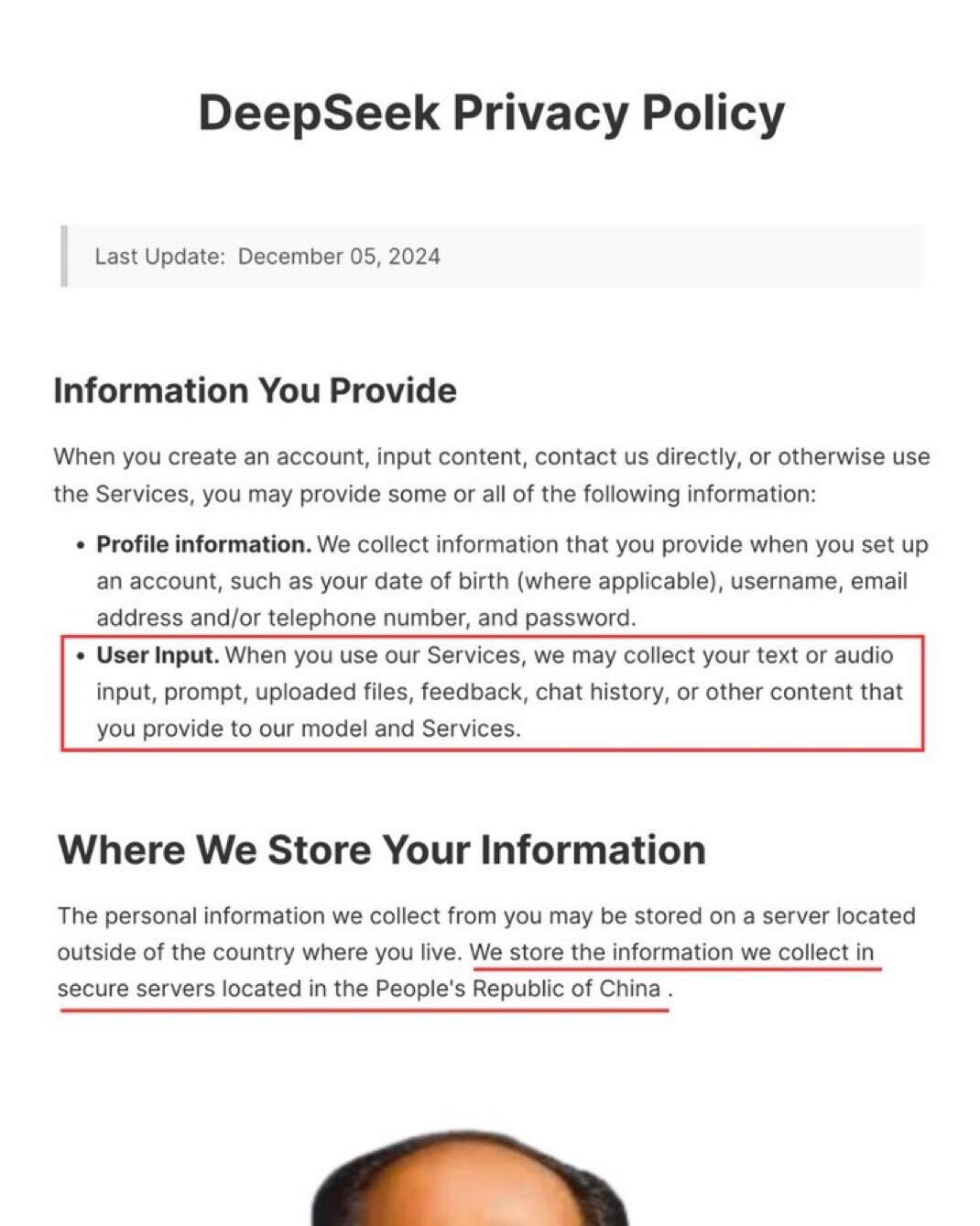
The biggest concern with DeepSeek is that it essentially gives the Chinese government a gateway to monitor DeepSeek users. In the West we have laws like CCPA and GDPR which prohibit the government from utilizing the private sector for government surveillance activities. But in China, data sovereignty laws grant the Chinese government extensive authority to access data when necessary for national security, public order, or economic management.
As outlined in the DeepSeek Privacy policy, DeepSeek explicitly sends user data, including chat messages, personal information, and device and user interactions to servers located in China. This raises concerns about what the Chinese government may do with this information. The U.S. Military has already been prohibited from using DeepSeek due to privacy and ethical concerns.
Espionage or Interference with U.S. Intelligence Operations
You might wonder, why does it matter if the Chinese government has your data? Your data is already floating around the U.S. and companies are using it to serve you targeted ads, drive website optimization, and sell to other companies upstream. This “I don’t care” sentiment was expressed by many Americans across social media during the TikTok ban scare.
However, your data does matter and it's important to exercise caution when exposing it to the Chinese government. Why? Because the Chinese government uses our data to harvest detailed profiles on individuals and groups. By running advanced analytics on these databases, the Chinese government can identify unusual patterns that may signal suspicious activity. By identifying potential state-backed spies and threats, China can implement additional monitoring, interfere with foreign intelligence operations, and drive their own espionage initiatives.
Content Censorship and Disinformation
DeepSeek's AI has been observed to censor topics deemed politically sensitive by the Chinese government, such as the 1989 Tiananmen Square protests and the status of Taiwan. This raises concerns about the dissemination of biased or incomplete information. If users at your organization are using DeepSeek, China could be curating the information they receive which may drive internal and external communications. In this way, China could influence the mainstream narrative in a way that benefits China, but leaves out important facts.

Information Bias
One report found that DeepSeek is 3x more biased than Claude 3 Opus. When prompted to generate biased outputs, DeepSeek showed an especially high appetite for expressing biases around race, religion, and health. Biases in AI models come from training data. If employees are using DeepSeek to inform decision making or communications, it could end up perpetuating negative stereotypes or discriminatory behavior, if left unchecked.
Fuel Chinese Competitive Intelligence
Employees may input sensitive corporate data, such as proprietary code, business strategies, or customer information, into tools like DeepSeek. Once the model has been exposed this cannot be undone. The Chinese government will have this information for good. In a world where world country-based economies are battling for dominance, exposing corporate information to China could give them a leg up on creating competitive products or services. By understanding what’s coming down the pike in terms of innovation and production, China can make data-driven decisions about where to invest resources or sanction certain exports that may hinder U.S. production.
Supply Chain Vulnerabilities
Deepseek was already hit with a large-scale cyber attack in late January, and this is just the beginning. And cloud security provider Wiz reported they discovered an exposed database leaking sensitive data, including chat history, secret keys, backend details, and other highly sensitive information such as API Secrets and operational metadata. The exposure allowed for complete database control and potential privilege escalation within the DeepSeek environment without requiring any authentication. At the time of this writing it's unclear whether or not malicious actors compromised the environment, but the situation underscores the threat of supply chain vulnerabilities for users accessing DeepSeek.
Insecure Code Generation
One report found that DeepSeek was 11x more likely to generate insecure code than OpenAI. Insecure code generation refers to the degree to which a model can be manipulated to generate malware or known malware signatures. Researchers at the Enkrypt AI Red Team found that DeepSeek, when prompted, would produce malicious code 78% of the time. That’s a severe security vulnerability, as this tool can easily be used to support malicious cyber activities.
How Reco Can Help
Want to know who at your organization is using DeepSeek? Reco can help. By monitoring over 140 app integrations and capturing authentication events from audit logs and API activity, Reco can detect DeepSeek users in real time. Gain instant visibility into who is accessing DeepSeek, how they're authenticating, and what permissions the app has. Use one-click controls to manage access through the Reco dashboard.


Think of Reco as your SaaS traffic controller. Reco spots when anyone in your organization who connects to DeepSeek with their corporate credentials so you can block access immediately.

Want to learn more about Reco? Schedule a demo today.

Merritt Baer
ABOUT THE AUTHOR
Merritt is the CISO at Reco and Advisor to a small handful of young companies including Expanso, Andesite, Enkrypt AI, and Level 6 Communications. Previously, Merritt served in the Office of the CISO at Amazon Web Services for over five years–a Deputy CISO to help to secure AWS infrastructure, at a vast scale. She has also worked in security in all three branches of the US government and the private sector, including the Federal Communications Commission, the US Department of Homeland Security, the Office of US Senator Michael Bennet, and the US Court of Appeals for the Armed Forces.

Merritt is the CISO at Reco and Advisor to a small handful of young companies including Expanso, Andesite, Enkrypt AI, and Level 6 Communications. Previously, Merritt served in the Office of the CISO at Amazon Web Services for over five years–a Deputy CISO to help to secure AWS infrastructure, at a vast scale. She has also worked in security in all three branches of the US government and the private sector, including the Federal Communications Commission, the US Department of Homeland Security, the Office of US Senator Michael Bennet, and the US Court of Appeals for the Armed Forces.



%201.svg)
.jpg)













